Bold BI Installation and Deployment on CentOS Environment
Deployment prerequisites
-
Install Apache.
-
Install the
GDIPluspackage using the following command:sudo dnf install https://dl.fedoraproject.org/pub/epel/epel-release-latest-8.noarch.rpm sudo yum install epel-release sudo yum install libgdiplus -
If you want to install the ETL application with Bold BI, follow these steps. Otherwise, skip this step and proceed with step 4.
-
Check and install
Python 3.9by executing the following command:sudo dnf groupinstall 'development tools' && sudo dnf install wget openssl-devel bzip2-devel libffi-devel && sudo curl https://www.python.org/ftp/python/3.9.2/Python-3.9.2.tgz -O && sudo tar -xvf Python-3.9.2.tgz && cd Python-3.9.2 && sudo ./configure --enable-optimizations && sudo make install -
Install
python pipand the following pip packages by running the following command.sudo yum -y install python3-pip && python3.9 -m pip install duckdb===1.1.2 dlt===0.5.4 pymysql pyodbc pg8000 poetry pandas===2.2.2 "dlt[parquet]" "dlt[filesystem]"
-
-
Add an
openssl confpath to the environment if does not exist:export OPENSSL_CONF=/etc/ssl/
Configuring the Bold BI application
-
Please register and download the Bold BI Linux package.
-
Download the Bold BI Linux package by running the following command:
sudo wget {Bold BI Linux package link} -
Extract the zip file:
sudo unzip {Bold BI Linux package zip file} -
Change the working directory to
BoldBIEnterpriseEdition-Linuxby running the following command:cd BoldBIEnterpriseEdition-Linux -
Execute the following command to deploy Bold BI in your Linux machine:
sudo bash install-boldbi.sh -i {new} -u {user} -h {host URL} -s apache -
i: Installation type: Specifies whether it is a new or upgrade installation.
-
u: Specify the user or group that manages the service.
-
h: Domain or IP address of the machine with HTTP protocol.
-
s: Setting this to “Apache” will automatically configure the Bold BI with the Apache front-end server.
IMPORTANT: If you have any existing applications running on the Linux machine using Apache, configure the Apache manually.
Example for new installation:
sudo bash install-boldbi.sh -i new -u www-data -h http://linux.example.com -s apache
Once the installation is completed, open the host URL in the browser and continue with the application startup.
Manually Configure Apache
To configure Apache as a reverse proxy to forward requests to the Bold BI app, modify the file /etc/httpd/sites-available/000-default.conf file.
- Open it in a text editor and add the following code.
<VirtualHost *:80>
#ServerName localhost
#Redirect / https://localhost/
#</VirtualHost>
#<VirtualHost *:443>
#ServerName localhost
ProxyRequests Off
ProxyPreserveHost On
Protocols h2 http/1.1
LimitRequestBody 209715200
Timeout 300
ProxyTimeout 300
#SSLEngine On
#SSLCertificateFile /path/to/certificate/file/domain.crt
#SSLCertificateKeyFile /path/to/key/file/domain.key
<Location />
ProxyPass http://localhost:6500/ Keepalive=On
ProxyPassReverse http://localhost:6500/
RewriteEngine on
RewriteCond %{HTTP:UPGRADE} ^WebSocket$ [NC]
RewriteCond %{HTTP:CONNECTION} Upgrade$ [NC]
RewriteRule /(.*) ws://localhost:6500/$1 [P]
RequestHeader set "X-Forwarded-Proto" expr=%{REQUEST_SCHEME}
</Location>
<Location /api>
ProxyPass http://localhost:6501/api Keepalive=On
ProxyPassReverse http://localhost:6501/api
RewriteEngine on
RewriteCond %{HTTP:UPGRADE} ^WebSocket$ [NC]
RewriteCond %{HTTP:CONNECTION} Upgrade$ [NC]
RewriteRule /api/(.*) ws://localhost:6501/api/$1 [P]
RequestHeader set "X-Forwarded-Proto" expr=%{REQUEST_SCHEME}
</Location>
<Location /ums>
ProxyPass http://localhost:6502/ums Keepalive=On
ProxyPassReverse http://localhost:6502/ums
RewriteEngine on
RewriteCond %{HTTP:UPGRADE} ^WebSocket$ [NC]
RewriteRule /ums/(.*) ws://localhost:6502/ums/$1 [P]
RequestHeader set "X-Forwarded-Proto" expr=%{REQUEST_SCHEME}
</Location>
# Start of bi locations
<Location /bi>
ProxyPass http://localhost:6504/bi Keepalive=On
ProxyPassReverse http://localhost:6504/bi
RewriteEngine on
RewriteCond %{HTTP:UPGRADE} ^WebSocket$ [NC]
RewriteRule /bi/(.*) ws://localhost:6504/bi/$1 [P]
RequestHeader set "X-Forwarded-Proto" expr=%{REQUEST_SCHEME}
</Location>
<Location /bi/api>
ProxyPass http://localhost:6505/bi/api Keepalive=On
ProxyPassReverse http://localhost:6505/bi/api
RewriteEngine on
RewriteCond %{HTTP:UPGRADE} ^WebSocket$ [NC]
RewriteCond %{HTTP:CONNECTION} Upgrade$ [NC]
RewriteRule /bi/api/(.*) ws://localhost:6505/bi/api/$1 [P]
RequestHeader set "X-Forwarded-Proto" expr=%{REQUEST_SCHEME}
</Location>
<Location /bi/jobs>
ProxyPass http://localhost:6506/bi/jobs Keepalive=On
ProxyPassReverse http://localhost:6506/bi/jobs
RewriteEngine on
RewriteCond %{HTTP:UPGRADE} ^WebSocket$ [NC]
RewriteCond %{HTTP:CONNECTION} Upgrade$ [NC]
RewriteRule /bi/jobs/(.*) ws://localhost:6506/bi/jobs/$1 [P]
RequestHeader set "X-Forwarded-Proto" expr=%{REQUEST_SCHEME}
</Location>
<Location /bi/designer>
ProxyPass http://localhost:6507/bi/designer Keepalive=On
ProxyPassReverse http://localhost:6507
RewriteEngine on
RewriteCond %{HTTP:UPGRADE} ^WebSocket$ [NC]
RewriteRule /bi/designer/(.*) ws://localhost:6507/bi/designer/$1 [P]
RequestHeader set "X-Forwarded-Proto" expr=%{REQUEST_SCHEME}
</Location>
<Location /bi/designer/helper>
RewriteEngine on
RewriteCond %{HTTP:UPGRADE} ^WebSocket$ [NC]
RewriteCond %{HTTP:CONNECTION} Upgrade$ [NC]
RewriteRule /bi/designer/helper(.*) ws://localhost:6507/bi/designer/helper$1 [P]
RequestHeader set "X-Forwarded-Proto" expr=%{REQUEST_SCHEME}
</Location>
<Location /aiservice>
ProxyPass http://localhost:6510/aiservice Keepalive=On
ProxyPassReverse http://localhost:6510/aiservice
RewriteEngine on
RewriteCond %{HTTP:UPGRADE} ^WebSocket$ [NC]
RewriteCond %{HTTP:CONNECTION} Upgrade$ [NC]
RewriteRule /bi/designer/helper(.*) ws://localhost:6510/aiservice$1 [P]
RequestHeader set "X-Forwarded-Proto" expr=%{REQUEST_SCHEME}
</Location>
# End of bi locations
</VirtualHost>
- If you need to configure the
Bold Data Hubalong with the Bold BI, you need to add the below syntax to the000-default.conffile after aiservice block.
<Location /etlservice/>
ProxyPass http://localhost:6509/ Keepalive=On
ProxyPassReverse http://localhost:6509/
RewriteEngine on
RewriteCond %{HTTP:UPGRADE} ^WebSocket$ [NC]
RewriteRule /etlservice/(.*) ws://localhost:6509/etlservice/\$1 [P]
RequestHeader set "X-Forwarded-Proto" expr=%{REQUEST_SCHEME}
</Location>
<Location /etlservice/_framework/blazor.server.js>
ProxyPass http://localhost:6509/_framework/blazor.server.js Keepalive=On
ProxyPassReverse http://localhost:6509/_framework/blazor.server.js
RewriteEngine on
RewriteCond %{HTTP:UPGRADE} ^WebSocket$ [NC]
RewriteRule /etlservice/_framework/blazor.server.js(.*) ws://localhost:6509/etlservice/_framework/blazor.server.js\$1 [P]
RequestHeader set "X-Forwarded-Proto" expr=%{REQUEST_SCHEME}
</Location>
Once the Apache configuration is established, run the command sudo apache2ctl configtest to verify the syntax of the configuration files. If the configuration file test is successful, force Apache to pick up the changes by running sudo systemctl restart httpd.
Configure SSL in Apache server
If you have an SSL certificate for your domain and need to configure the site with it, follow these steps or you can skip this:
-
Install mod_ssl and restart the apache service by running the following command:
sudo yum install mod_ssl sudo systemctl restart httpd -
Navigate to the directory
/etc/httpd/sites-available/and open the fileboldbi-apache-config.confin a text editor. -
Uncomment the marked lines in the Apache config file.
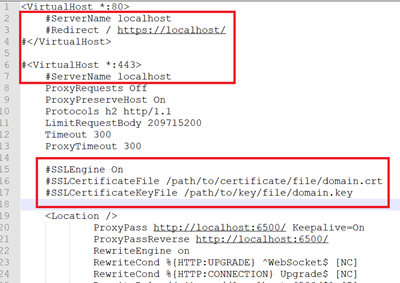
-
Replace “localhost” with your domain.
-
Define the path of the SSL certificate:
ssl_certificate /etc/ssl/domain.crt. -
Specify the directory where the SSL certificate key is located:
ssl_certificate_key /etc/ssl/domain.key.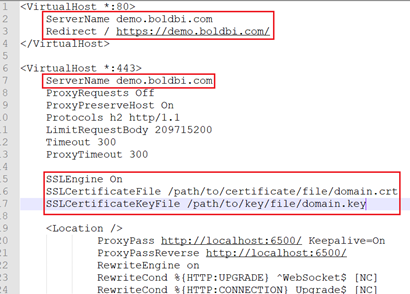
-
Save the changes and run
sudo apachectl configtestto verify the syntax of the configuration file. If the configuration file test is successful, force Apache to pick up the changes by runningsudo systemctl restart httpd.
NOTE: If you are configuring the application with SSL, you need to update the URLs in the product.json file with
HTTPSlocated in/var/www/bold-services/application/app_data/configuration.
Next steps
- Deployment prerequisites
- Configuring the Bold BI application
- Manually Configure Apache
- Configure SSL in Apache server
- Next steps
Having trouble getting help?
Contact Support- Deployment prerequisites
- Configuring the Bold BI application
- Manually Configure Apache
- Configure SSL in Apache server
- Next steps
Having trouble getting help?
Contact Support